Protecting your Australian business from cyber threats is paramount. The ACSC Essential Eight offers a crucial baseline of eight mitigation strategies to significantly reduce your risk. Let’s understand why it matters.
What is the Essential Eight?
The Essential Eight are key cybersecurity strategies recommended by the ACSC:
The strategies cover three key areas:
Preventing malware delivery and execution.
Limiting the extent of cybersecurity incidents.
Recovering data and system availability.
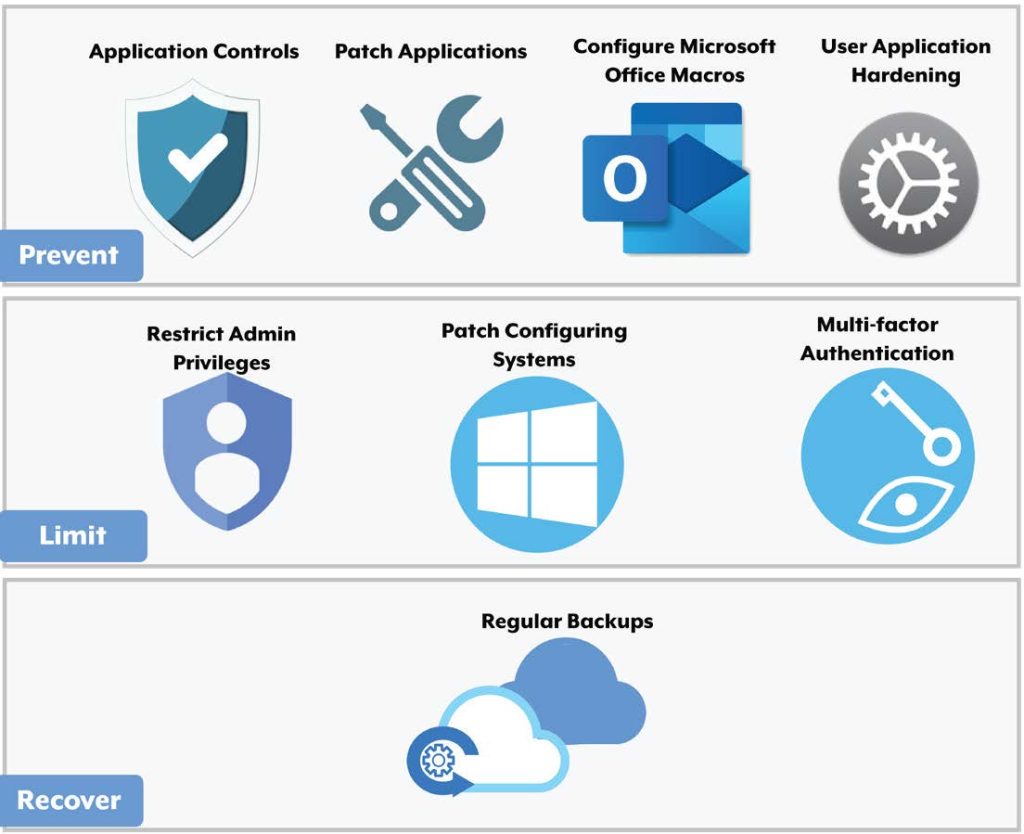
- Application Control
- Patching Applications
- Configuring Microsoft Office Macro Settings
- User Application Hardening
- Restricting Administrative Privileges
- Patching Operating Systems
- Multi-Factor Authentication (MFA)
- Regular Backups
There are four levels:
- Maturity Level 0 (ML0): Indicates significant weaknesses in the organisation’s overall cyber risk posture. Controls might be missing, partially deployed, or ineffective.
- Maturity Level 1 (ML1): Focuses on mitigating threats from adversaries primarily using common tools and techniques to gain initial access. This is often considered the minimum baseline for most organisations. It involves implementing the controls in a foundational way.
- Maturity Level 2 (ML2): Builds upon ML1. It requires more robust implementation and focuses on managing risks from adversaries operating with better tradecraft and tools, who are more adept at bypassing basic security measures.
- Maturity Level 3 (ML3): Represents the highest level of maturity. It focuses on mitigating risks from more sophisticated adversaries, including state-sponsored actors, who use advanced techniques, tools, and exploits. This level involves advanced hardening, monitoring, and response capabilities.
What Maturity Level Should Your Business Aim For?
The target Maturity Level depends on your organisation’s specific risk profile:
- What kind of data do you handle? (Sensitive personal info, financial data, intellectual property?)
- What are the consequences if your systems are breached? (Financial loss, reputational damage, operational disruption?)
- Who might target you? (Opportunistic hackers, organised crime, state actors?)
While Maturity Level 1 is often the recommended starting point for most businesses, organisations facing higher risks should aim for Maturity Level 2 or 3. Importantly, your target level might differ for each of the eight controls based on specific risks and implementation costs.
The Path Forward: Assessment and Improvement
- Assessment: The first step is understanding where you stand. A thorough Essential Eight assessment will evaluate your current implementation of each control against the Maturity Level criteria. This identifies your current level and highlights specific gaps.
- Planning: Based on the assessment and your target maturity level(s), create a tailored implementation plan. Prioritise the controls and actions that will provide the biggest security improvements for your specific situation.
- Implementation: Deploy the necessary technical configurations, policies, and user training.
- Monitoring & Support: Cybersecurity is an ongoing process. Continuously monitor your controls, adapt to new threats, and ensure your implementation remains effective. Regular reassessments are vital.
Strengthen Your Security Today
The Essential Eight, combined with the Maturity Level framework, provides a practical, actionable path to significantly improve your organisation’s cybersecurity posture. Don’t wait for an incident to force your hand. Understanding your current maturity and taking steps to improve is one of the best investments you can make in your business’s future resilience.
Ready to find out your Essential Eight Maturity Level? Contact a cybersecurity professional for a comprehensive assessment and start building a stronger defence today.